Design Review
Perform a cybersecurity check on the design of your new and existing IT Systems
> IT | PENTESTING & MORE > Design Review
Perform a cybersecurity check on the design of your new and existing IT Systems
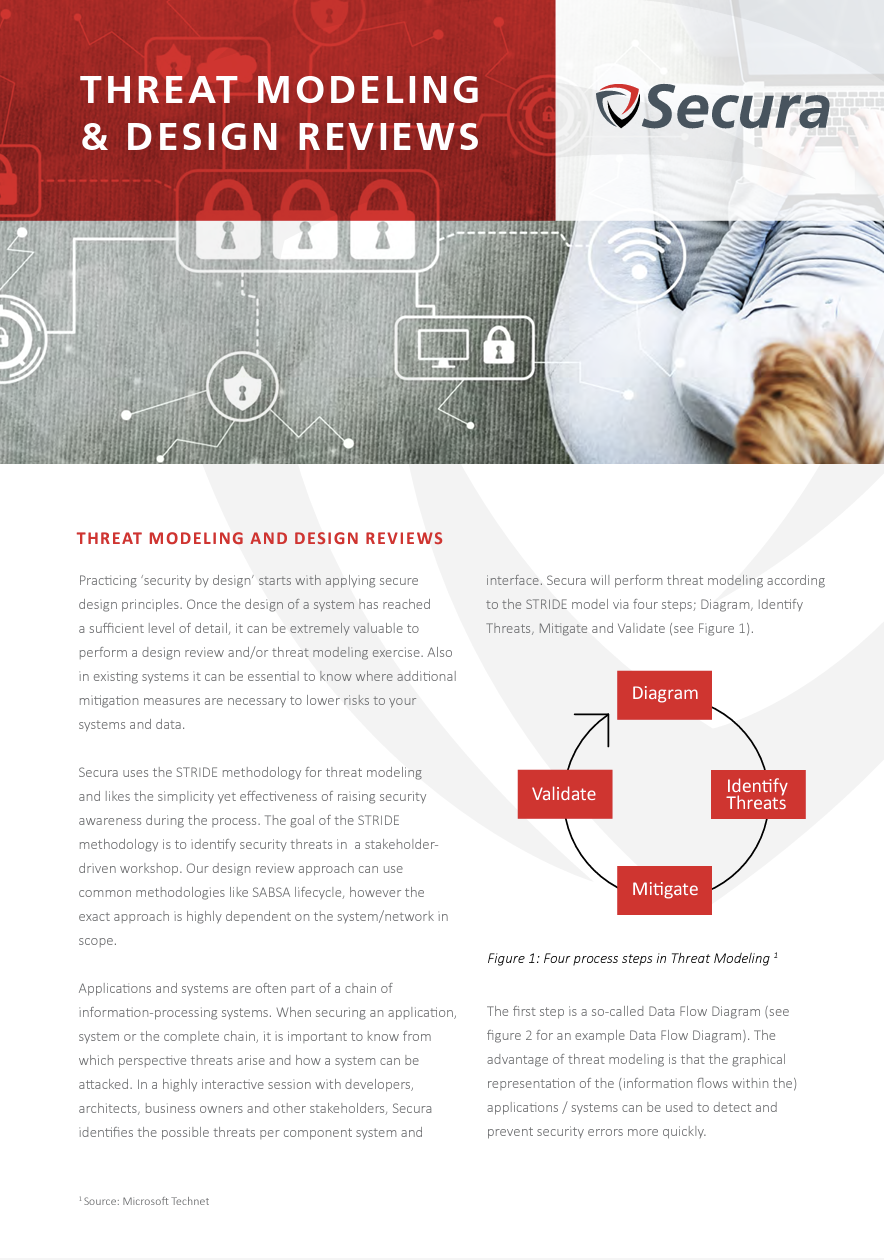
Once the design of a system has reached sufficient detail, it can be valuable to perform a design review.
Also in existing systems, it can be essential to look at the design with today’s security threats to know where additional mitigation measures are necessary to lower risks to your systems and data. Secura's Design Review aims to identify security improvements that are applicable to the environment as early as possible, to prevent design decisions from turning into costly production changes, or disastrous data leaks.
In a design review, Secura will review all available (relevant) design documentation and discuss this with your architect, technical owner and/or developers. The benefit of a design review is that the design can be verified against the information security policies (if available) and best practices of your organization.
Download Fact Sheet
Download Fact Sheet on Secura's Design Review Service
Mitigate security risks by identifying design flaws & potential threats and attack paths early on.
DownloadCONTACT ME ABOUT A DESIGN REVIEW
Would you like to learn more about our Design Review Service? Please fill out the form below, and we will contact you within one business day.

Related Services
Threat Modeling
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.









