OT Perimeter Assessment
Protecting the link between IT and OT networks is crucial to secure the OT attack surface. Our OT Perimeter Assessment can help you keep your OT systems secure.
> OT | SITE ASSESSMENT & MORE > OT Perimeter Assessment
OT Perimeter Assessment
Boundaries between Information Technology (IT) and Operational Technology (OT) are fading. Protecting the link between IT and OT networks is now crucial to secure the OT attack surface. Our OT Perimeter Assessment can help you keep your OT systems secure.

Gain insight into threats to your OT systems

Uncover vulnerabilities

Get advice from OT security experts
Why choose the OT Perimeter Assessment?
IT and OT networks are increasingly linked - for automation, efficiency, and instant data analysis. This IT/OT convergence is a result of Industry 4.0, the fourth revolution in industrial manufacturing. It makes your systems more vulnerable to cyber attacks - particularly if they are also connected to the internet and the cloud.
You could compare your OT network to for instance a city. The city used to be a relatively small village, with roads, byways and connections that were well-known to everybody in the village. Over time the village grew: the small roads became lanes, with infinitely more traffic connecting travelers from all over the world to the city. It can be now hard to keep track not only of the layout of the city, but of the movement of the traffic and of potential weak spots that malicious visitors could use to gain access to important quarters.
To make sure malicious visitors can't reach crucial parts of the city, it makes sense to first check the entry points around the city for vulnerabilities - the place where the OT network connects to the IT network - before you check the smallest alleyways or back streets deep in the city.

Frank Ruedisueli
OT Security Lead
Secura
Some companies do not know which assets they have in their OT network and which connections these have to the network. This assessment helps you find out.
What to expect of the assessment
Our experts examine and analyze these three things: your OT-network design, the flow of data traffic and vulnerabilities in the network. We focus on systems in the IT and OT networks that need to communicate with each other. This includes IT systems that interact with dual-homed IT/OT systems or cross the Demilitarized Zone (DMZ). The assessment covers OT devices in Level 3 of the Purdue model that exchange information with the IT network.

A good place to start
The OT Perimeter Assessment is an excellent place to start with OT security: it gives you instant and relevant insights on risks to your IT/OT connections. It also gives you recommendations on measures that can significantly increase your security. If you already have OT security measures in place, this assessment verifies if these measures work as intended.
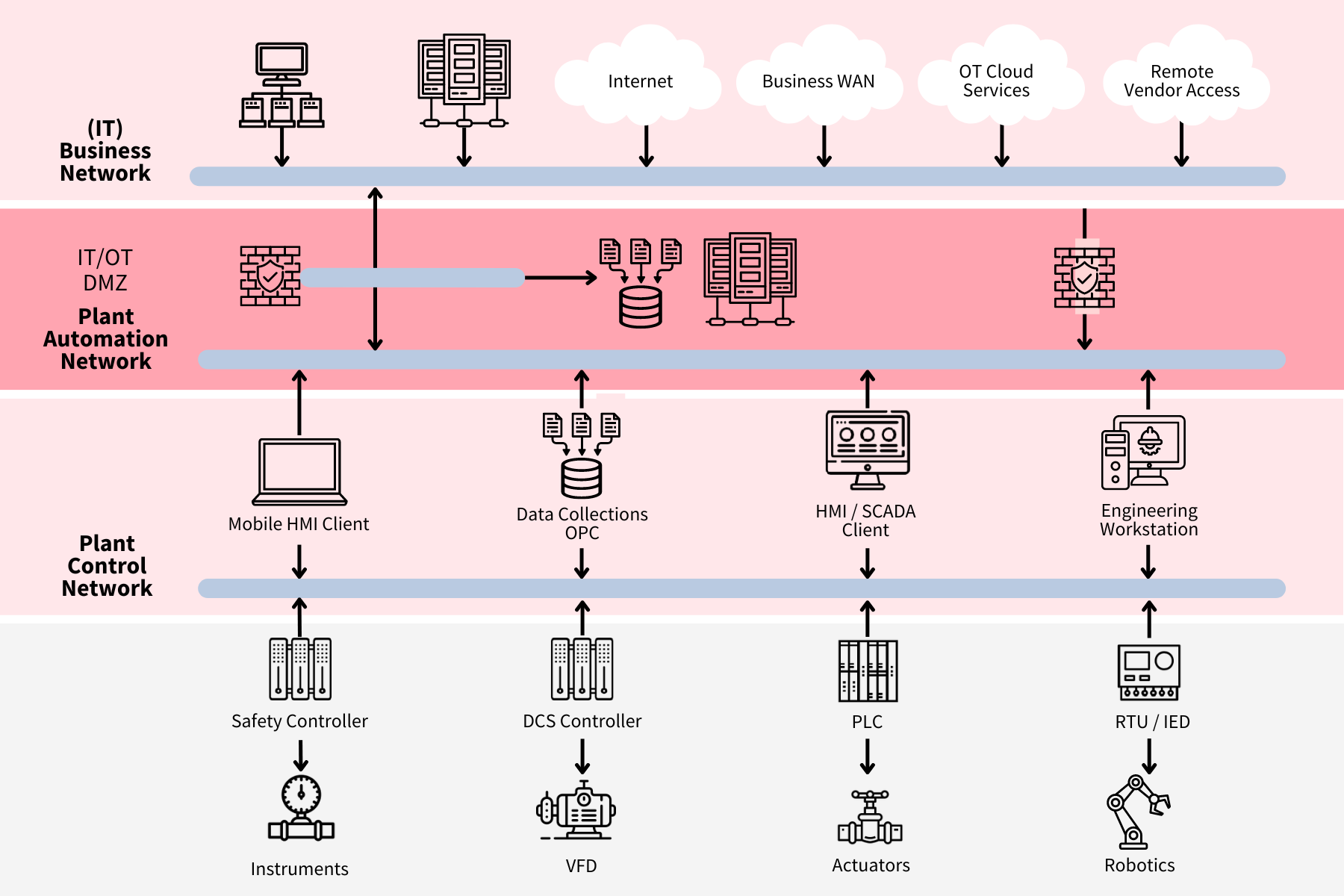
This graphic shows the focus of the OT Perimeter Assessment. The main focus, in red, is the perimeter between IT and OT. However, we also check relevant parts of the OT or IT systems (in pink).
How the OT Perimeter Assessment works
01
Understanding the OT network design
After studying drawings, asset registers and technical info, we draw up a network diagram. Your experts and ours then review this, to pinpoint all possible entry points, including remote UPS management, physical access controls, or HVAC and BMS (building management system). Your IT and OT experts are also involved in a high-level Threat Modeling session, to map potential threats.
02
Analyzing the firewall configuration
The traffic between your IT and OT is probably filtered by one or more firewalls or other boundary protection devices. We analyze the firewall settings thoroughly. The goal is to:
- Verify that only the minimum amount of required traffic is allowed through and all other traffic is denied.
- Verify that allowed traffic only flows between authorized endpoints.
- Correlate the allowed traffic to the security configurations of the endpoints.
03
Scanning for vulnerabilities
Based on the analyzed network diagrams and firewall configuration, you can expect additional OT network scans to get a more in depth insight into the actual network traffic. We use two different techniques:
- Passive scanning. This is a “read-only” technique that uses a copy of already existing network traffic. method can expose vulnerabilities like weak protocols, poor configuration or outdated firmware.
- Active scanning. These queries will be tailored to a single host or a selected part of the network. This way we can discover weak or unencrypted protocols, weak or unsecure software applications or services, unknown IT/OT communication flows, unknown systems or poorly configured systems and known security vulnerabilities (CVEs).
04
You can now take action
All the findings from these three steps are then combined and analyzed. The result is a report with actionable points of improvement, so you can take direct action.

Brochure OT Perimeter Assessment (ENG)
Read about the OT Perimeter Assessment in this brochure.
DownloadOT Services
NIS2 Services
OT Site Assessment
Contact me
Do you want to know more about how we can help you with your OT security? Fill out the form and we will get back to you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.











