Social Engineering Services
Empower your organization by raising the cybersecurity awareness of your people.
> Services for your people > Social Engineering Services
The human factor could be the weakest link in your cybersecurity
The technical security of systems is improving all the time. To still gain access to your networks and systems, cybercriminals use social engineering. They impersonate someone else and manipulate employees into handing over sensitive data. The best-known form is e-mail phishing, but social engineering can also be done by phone or physically. We can help raise awareness with e-mail phishing simulations and other Social Engineering Services.

Raise the cyber resilience of your people

A tailored approach to suit your needs

Expertise in social engineering tactics

Sophie Jellema
Senior Social Engineer
Secura
Our consultants use scenarios and tactics that a real attacker might employ. The most important part of a social engineering project is the debrief: we always explain what we do to your employees.

YOUR CHALLENGES
- How to train your people to effectively mitigate the risks posed by social engineering
- How to keep your people aware of the latest social engineering techniques
- How to balance security and usability without impeding efficiency or employee morale.
HOW WE SUPPORT YOU
Secura helps large and medium sized organizations all over Europe raise their cyber resilience. We know the importance of arming your people against social engineering tactics like telephone phishing, and we know how to do this.
With our Social Engineering Services, we can help you to:
- Train your people to effectively mitigate the risks posed by social engineering
- Keep your people aware of the latest social engineering techniques
- Balance security and usability without impeding efficiency or employee morale
OUR SOCIAL ENGINEERING SERVICES
01
E-mail phishing simulation
We conduct phishing attempts on your employees via e-mail messages and e-mail attachments. Depending on your needs we customize our approach.
- Broad phishing attempt of all employees with standardized scenario's for training and awareness purposes. This type is especially good to measure the progress of awareness campaigns over time.
- Targeted spearphishing with the goal of extracting credentials from employees. The scenarios are based on OSINT (Open Source Intelligence) data collected about your organization and employees. This type of phishing service resembles a real world attacker specifically targeting your organization.
- Custom phishing that is specifically tailored to your needs. For example phishing with malicious office documents to emulate real world Advanced Persistent Threat groups or ransomware infection vectors.
Read More: Phishing Awareness
02
Telephone phishing
We call a number of your employees pretending to be from a trusted organization and try to trick them into sharing sensitive information over the phone. We use urgency and fear tactics that criminal attackers use.
You receive anonymized video footage of the investigation that you can use to train other employees. This is an effective learning method.
03
MYSTERY GUEST assessment
During a Mystery Guest Assessment, our ethical social engineers try to gain physical access to your offices and premises. They then try to gather information present on desks and workstations, in documents, archives and on the internal company network, through workstations, printers or network connections.
04
Phishing specials
Besides e-mail phishing and telephone phishing, cybercriminals also use other forms of deception, for example, phishing via SMS, or ‘smishing’. You can employ our social engineers for the following tactics to test your resilience:
- USB-phishing: attackers leave or give away a USB flash drive with malware on it. If someone plugs the USB into a computer, the attacker can gain access.
- SMS-phishing, or smishing, involves scammers sending fake text or instant messages. They pressure people with messages that appear urgent and then ask people to click on a link or share personal information.
- QR phishing, or quishing, uses QR codes that lead to a malicious website after scanning. Scammers try to trick people into scanning this QR code, with the aim of stealing personal information or installing malware.
05
SPOT THE MOLE GAME
Increase alertness for unknown individuals within your company with the game "Spot the Mole". This Incognito Challenge encourages employees to approach unknown individuals.
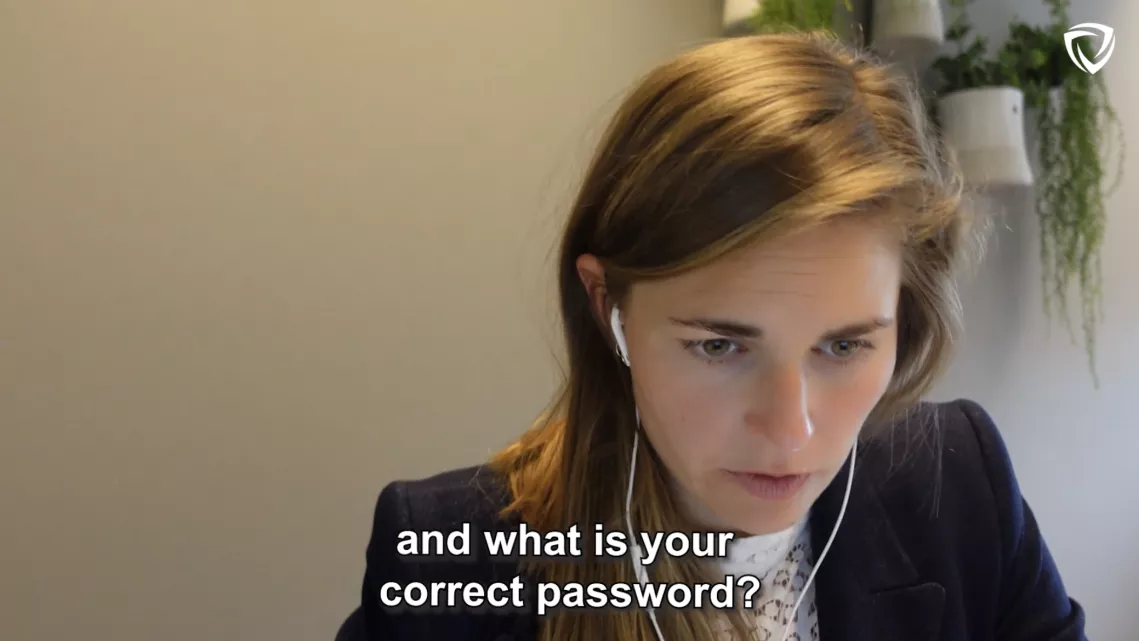
Video: Telephone Phishing demo - 49% of the employees we phoned shared their password within 3 minutes.
Download Fact sheet

CONTACT ME ABOUT SOCIAL ENGINEERING AWARENESS
Would you like to learn more about our Social Engineering Service? Please fill out the form below and we will get back to you within one business day.

Related Services
Cybersecurity Awareness E-Learning
Phishing Awareness Program
SAFE - Security Awareness & Behavior Program
Ransomware Resilience Assessment
Hacker Mindset Workshop
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.