Industrial VAPT
Vulnerability assessment and penetration testing (VAPT) are ways to discover weak spots in the security of your OT Systems
> OT | SITE ASSESSMENT & MORE > Industrial VAPT
Penetration Testing in an Industrial Environment
Within industrial environments, cybersecurity testing requires a specialized approach. This is due to the different risks and threat models within Operational Technology (OT).
Discover more about VAPT in the Industrial Sector:

What is Vulnerability Assessment & Penetration Testing?
Many types of testing are collectively known as Vulnerability Assessments and Penetration Testing’(VAPT). Classical Penetration Testing means that tests are performed from an attacker’s perspective, and vulnerabilities are exploited to see ‘how far can an attacker get’. However, this is not always the most effective way of testing because it often makes more sense to perform a Vulnerability Assessment.
A Vulnerability Assessment implies testing in such a way as to find as many vulnerabilities as possible without wasting time exploiting those vulnerabilities to see how far you can get. Finding more vulnerabilities is often more valuable because it reduces risks more effectively: exploring wide, instead of (only) deep.
The value of VAPT in OT
The aim of a penetration test is to illustrate as clearly as possible what the consequences of a certain issue with your cybersecurity could be, and what that would mean to your organization. For example, the risk that an IT security incident, like ransomware, could also affect the OT network, threat actors breaking into the OT network to access the intellectual property, supply chain risks caused by remote vendor connectivity, or the potential impact of a cyber-physical attack.
VAPT provides insight into the current cyber resilience of the IT and/or OT networks for these kinds of threats and if improvements might be required. Secura records the outcomes of the VAPT test in a clear report with a concise management summary, an extensive risk analysis for each outcome, and recommendations on a strategic, tactical, and operational level. The results of the assessment can be used to take steps to close security gaps and reduce the risk in your organization.
VAPT in the Industrial Sector
Within industrial environments, many critical business processes depend on OT. Networks with Industrial Controls Systems (ICS) such as DCS, PLC’s and SCADA systems manage and automate critical processes. Still, the enterprise’s IT services are just as important for daily operations. Moreover, due to the convergence of IT and OT and Industry 4.0-initiatives, the dependency between these two environments is also increasing. A successful business depends on reliable systems in both IT and OT; therefore, VAPT testing is important for all these systems. Different technologies are used across these environments, and it is collectively known that OT systems might not be resilient against VAPT scans. It is obvious that each area requires a different approach.
Scoping the VAPT assessment
Scoping the VAPT assessment is important. The different approaches for specific parts of the infrastructure are briefly described below by using a common reference model. Each infrastructure will be different, and therefore Secura will always start by reviewing the network topology with the customer to tailor our approach to the systems in scope.
- Informational Technology (IT)
- IT/OT-DMZ
- Operational Technology (OT)
- Internet of Things (IIoT)
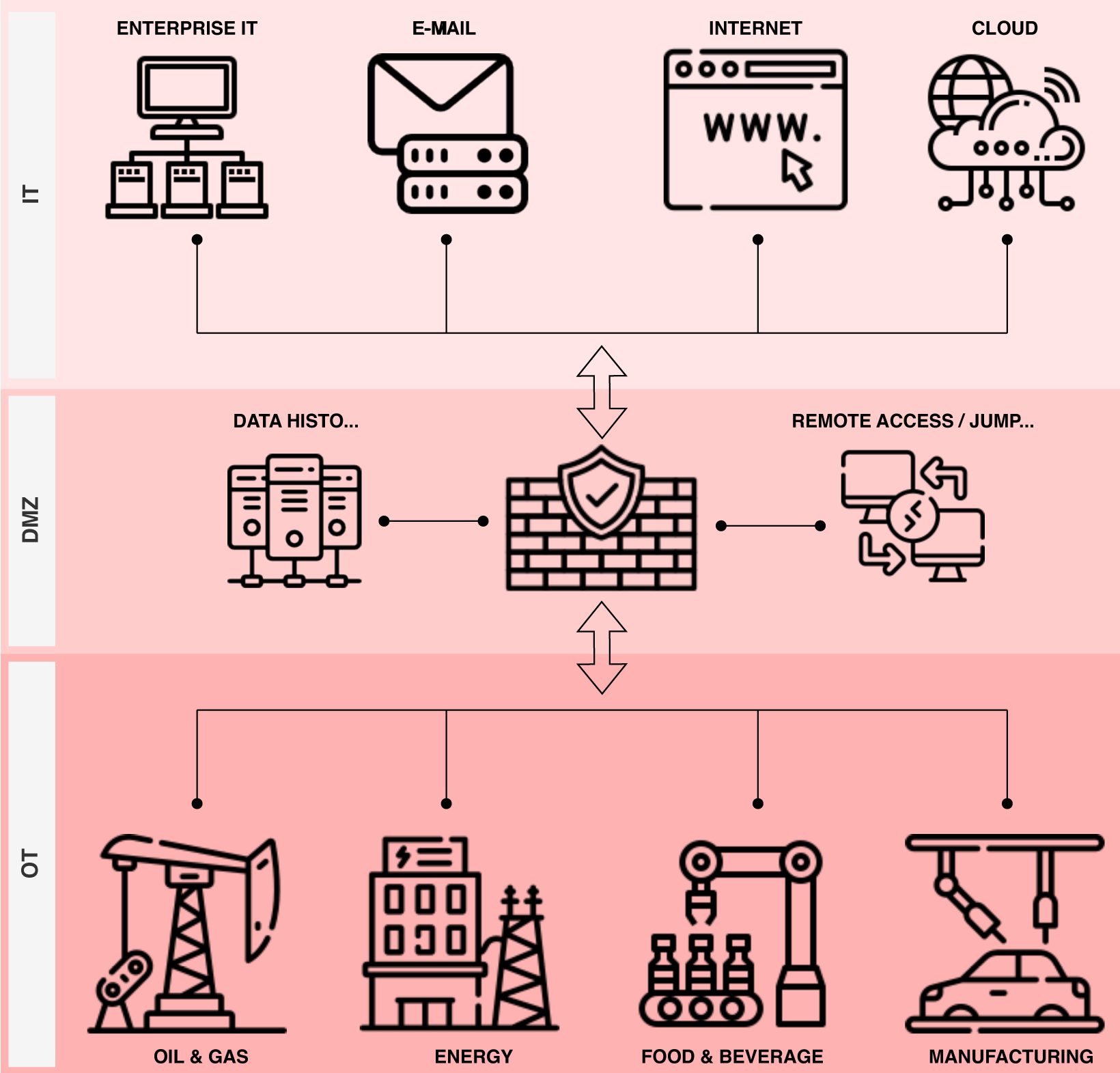
Scoping - Specific parts of the infrastructure
01
Information Technology (IT)
Besides all the regular components found in any modern IT network (and their related vulnerabilities), industrial organizations might face additional challenges. Services that depend on data received from the OT layer or vice versa. A good example is connecting the IT ERP system and OT applications, often using unencrypted SQL or HTTP connections. Even OT-cloud services or OT-remote access might be routed through the IT domain. This connectivity and dependency increase the risk that cyber incidents traverse between these domains. Incidents within the IT environment could affect the OT environment, but the opposite is also true.
Of course, you can have a standard VAPT performed within your IT domain. Still, it is also possible to extend this with the question if whether vulnerabilities in the IT domain could be abused to reach or affect the OT systems. In this case, we try to exploit the discovered vulnerabilities to gain access to servers in the IT/OT-DMZ or potentially directly in the OT network.
02
IT/OT-DMZ
THE DMZ separates the enterprise IT network and the OT network. Often, this level consists of generic IT components, but it could also contain specific OT-related applications, including specific OT communication protocols, like Modbus, OPC, or OPC-UA. Some examples are remote access servers, patch update distribution servers, and data historian servers. It is often a crucial layer as this is one of the first layers of defense of the underlying OT systems.
In general, these systems are more resilient against vulnerability scans. Therefore, we often suggest using a “grey box” approach. We get some information in advance to prevent disruptive techniques on systems that might not be able to cope with these attacks. At the same time, most tests use a realistic “hackers approach”. One of the main questions here is to check if vulnerabilities exist that could be leveraged by an attacker to get access to OT data or systems.
During the penetration test, attempts are made to escape from the DMZ constraints, either by moving laterally to other systems in the DMZ, escalating privileges, or exploiting security or configuration vulnerabilities. It will be investigated whether it is possible to manipulate communication between IT and OT (like production setpoint changes, remote operations, etc.). Still, the ultimate goal is to bypass the firewall and gain access to the OT domain.
03
Operational Technology (OT)
Within the OT environment, there are many more components like DCS controllers, PLC’s, RTU’s, SCADA systems, and possible other legacy systems that can’t handle the disruptive scans or actions used during a conventional penetration test. Even a simple network scan could already be sufficient to disrupt the working of a PLC. This is one of the reasons why it’s commonly said that it is not a good idea to perform VAPT assignments in live production networks.
Meanwhile, hackers might not know or care about this, and we know that many vulnerabilities exist in OT networks. So, how can you manage this? Instead of just following the consensus, you need to focus on tests that are possible in OT environments. This depends on the specific infrastructure in scope, but we generally prefer a “crystal box” approach. In this case, the information about the internal network is provided, maybe with some credentials and access to configuration examples. This information is needed so the approach for each device can be tailored based on where it “lives” in relation to the Purdue model.
VAPT techniques for OT systems
Passive scanning
One of the techniques that can be used in OT environments is passive vulnerability scanning. Contrary to normal (active) vulnerability scanning, there is no (intrusive) traffic injected into the network to ensure even the most fragile systems are not affected. Passive scanning is a “read-only” technique that uses a copy of already existing network traffic. This traffic is analyzed and could expose vulnerabilities like weak protocols, poor configuration, or outdated firmware.
The downside of this method is it is less accurate and will not provide full coverage (only devices in use at the time of testing will generate traffic to be analyzed). It will therefore require a bit more manual investigation to confirm the findings.
Selective scanning
On top of passive scanning, it is possible to use specific and less intrusive active scanning techniques in collaboration with the customer. These queries will be tailored to a single host or a selected part of the network, and parameters will be configured in such a way as to prevent any overwhelming amount of traffic. This technique is more accurate than passive scanning, but it’s time-consuming. Still, some devices like legacy PLCs should never be scanned when they are in production. However, it might still be possible to perform these scans during a maintenance period or manual supervision, or if available, in a separate test environment containing the same types of devices.
Secura’s approach in VAPT for OT
Our specific VAPT approach in the OT environment depends on which levels are in scope from the Purdue levels.
The Purdue Model
According to the Purdue model, a typical OT network consists of different levels:
Purdue Level 2 & 3
Generally, systems that reside in Purdue levels 2 and 3 (Area Supervisory and Site Operations, respectively) are based on generic IT components. Depending on the criticality of each system, we can use more or less intrusive methods. The question is often to test how resilient the systems and network are against targeted attacks. In these levels, systems may also use OT-specific protocols, like Modbus, DNP3, IEC-101/104, CIP Ethernet/IP, etc., to communicate to each other and to systems in the lower Purdue models. It is also not uncommon within OT environments that custom applications or solutions are installed on this level that might add an attack surface. The ultimate question is whether a hacker can move laterally over the network and to the deeper levels of the system.
In the penetration test stage, we try to exploit vulnerabilities in the system configurations, installed (custom) applications, weak IT protocols like FTP, Telnet, HTTP, and SNMP, and insecure industrial protocols. The goal is to gain access to engineering workstations, SCADA databases, or human-machine interfaces to investigate if we could influence the process.
Purdue Level 0 & 1
In level 1 (Basic control) and level 0 (Process), we will not use any intrusive methods unless it is specifically requested, for example, when the system could also be operated manually or is not in active use due to a scheduled maintenance period. Often, the question is whether an attacker can manipulate signals or measurements or carry out a cyber-physical attack, especially when this level might also contain safety systems (SIS). It is also possible to research if these lower levels (that might be installed in unmanned remote locations) can provide access to higher levels of the OT network and maybe even the IT environment.
In these levels, most of the communication is performed via OT-specific protocols, of which many are insecure. Some examples are, Modbus-TCP, Fieldbus, Profibus, HART, and many more, including vendor-proprietary protocols.
On request, we could, as part of the penetration test, investigate the possible vulnerabilities in these levels as well. We will try to exploit vulnerabilities in the used communication protocols, potential vulnerabilities in the controller’s or device firmware, or abuse weaknesses in the device configuration.
Connectivity
Finally, all these components are connected via network devices such as switches, routers, firewalls, and even wireless access points. On top of that, it is also common that a lot of protocol and media converters are used in OT environments, like RS-232/RS-485 to Ethernet or Copper to Optical Fiber converters. All these intelligent devices generate additional attack surfaces. Therefore, network configuration and segmentation are crucial and a good focus area for our VAPT service. These devices are resilient for these types of scans and will be included in the scope of regular vulnerability scans and tests.
During the penetration test, we try to abuse weaknesses in the configuration of these devices or exploit potential vulnerabilities in the firmware to gain access to the infrastructure layer. If succeeded, it becomes easier to attack other network parts, manipulate network traffic to influence the process, or eavesdrop on unencrypted communication.
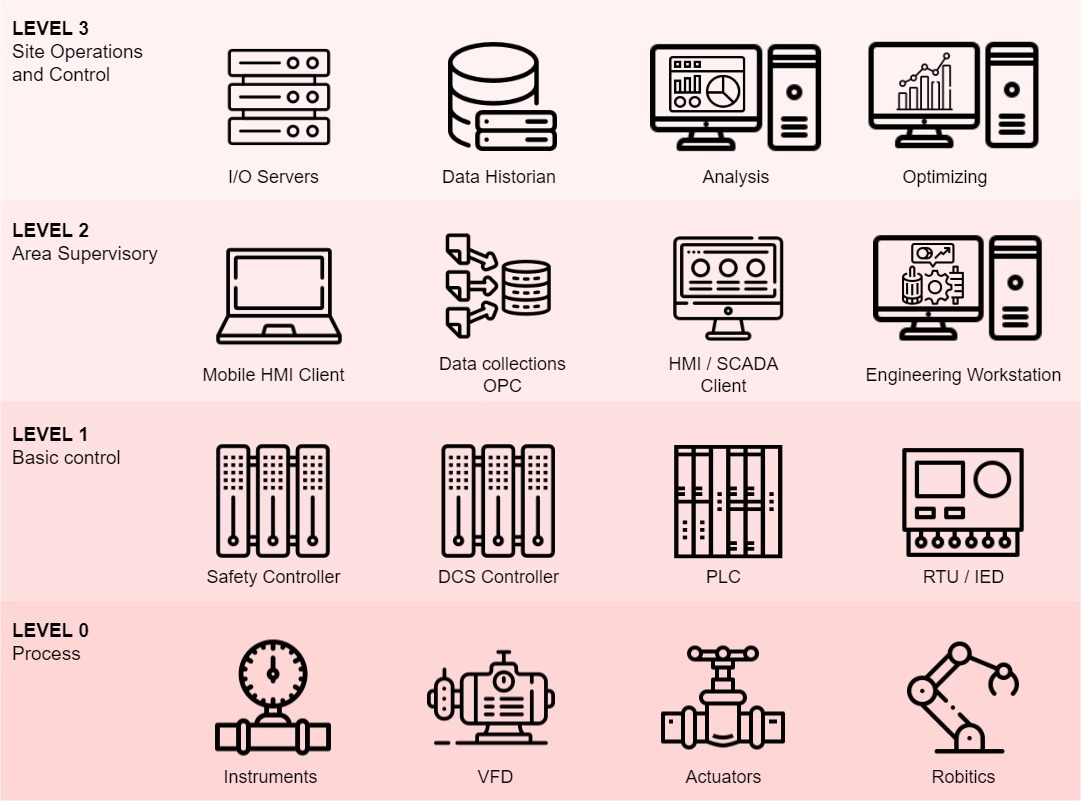
- Level 0 – Process
This level contains devices that physically interact with the process. For example, field instruments, variable frequency drives (VDF), pumps, motors, actuators, and robotics.
- Level 1 – Basic Control
This level contains the controllers that interact with the field instruments and actuators. For example, DCS and Safety controllers, Programmable Logic Controllers (PLC), and Remote Terminal Units (RTU).
- Level 2 – Area Supervisory
This level contains the devices used to monitor or interact with the controllers. For example, Human Machine Interfaces (HMI), Engineering workstations (EWS), and OPC data collectors.
- Level 3 – Site Operations and Controls
This level contains a system to support site-wide operations, maintenance, and optimizations. For example, data historians, I/O servers, and more generic security services for the OT environment like Domain Controllers, backup servers, and patch & AV distribution servers.
Download Fact Sheet

Download fact sheet on Industrial VAPT
Vulnerability Assessment and Penetration Testing (VAPT) in Industrial Environments
DownloadI'd like to learn more about Industrial Pentesting
Please fill out the form below and we will contact you within one business day.

Related Services
Site Assessment
Threat Modeling for Industrial Control Systems
OT Cyber FAT/SAT
OT Cybersecurity Fundamentals Training
Vulnerability Assessment / Penetration Testing (VAPT)
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.

















