RED WIZARD - USER FRIENDLY, AUTOMATED INFRASTRUCTURE FOR RED TEAM - PART 1
Author: Ben Brücker, Senior Security Specialist and Domain Manager Red Teaming at Secura.
Where to get it? https://github.com/SecuraBV/RedWizard
This is part of a blog series about Red Wizard. The first part will focus on the background of the tool. Future instances will focus on the technical implementation and the extensibility of the tool.
WHAT IS RED WIZARD?
Red Wizard is an open-source tool designed to provide repeatable, OPSEC-safe infrastructure for Red Teaming operations. Red Wizard was created to address the challenge faced by many serious Red Teams, where publicly available deployments are either limited or not user-friendly, requiring additional time and work from infrastructure maintainers and operators.
This tool automates the deployment of a comprehensive infrastructure with redirectors, backend systems, phishing relays, OSINT machines, and more. It is designed to be user-friendly, providing wizards to walk administrators and Red Team operators through the deployment process. The infrastructure is also self-documenting, making the sharing of all relevant details to the team of operators an effortless task.
EXAMPLE
Below you find an example of a moderately complex Red Teaming infrastructure that takes approximately 10 minutes to configure, and 30 minutes to deploy. It includes OSINT machines, 2 phishing servers, a CobaltStrike instance, a generic callback catcher and a backend for hardware implants:
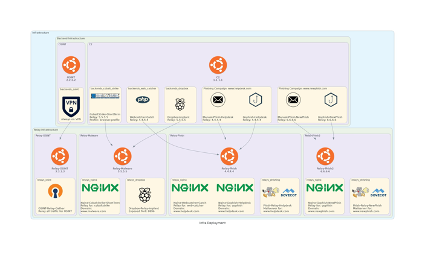
This diagram was created by Red Wizard as well, making it easy to share relevant information with your team.
WHAT RED WIZARD CAN DO
Red Wizard will help you provision your servers and install all necessary tools, tunnels and defaults.
It does not currently provision the underlying servers, as every company has their own processes for spinning up systems. That is why there are 4 very basic requirements that you can automate with for example terraform:
- Ubuntu 22.04 on the deployment system (Your laptop or a VM is fine)
- Clean Ubuntu 20.04 on all target machines (Will support 22.04 in the near future)
- 1 deployment user (Configured for key-based SSH access on all machines)
- Deployment user has identical sudo password on all machines
CURRENTLY PUBLICLY RELEASED PARTS
Currently the following 6 components are released that are quite common to Red Teaming operations:

Future releases might include:
- RedElk integration (Red Team SIEM by Outflank)
- MitM Phishing (EvilGinx / Modlishka)
- Support for non-standard relays (domain fronting etc)
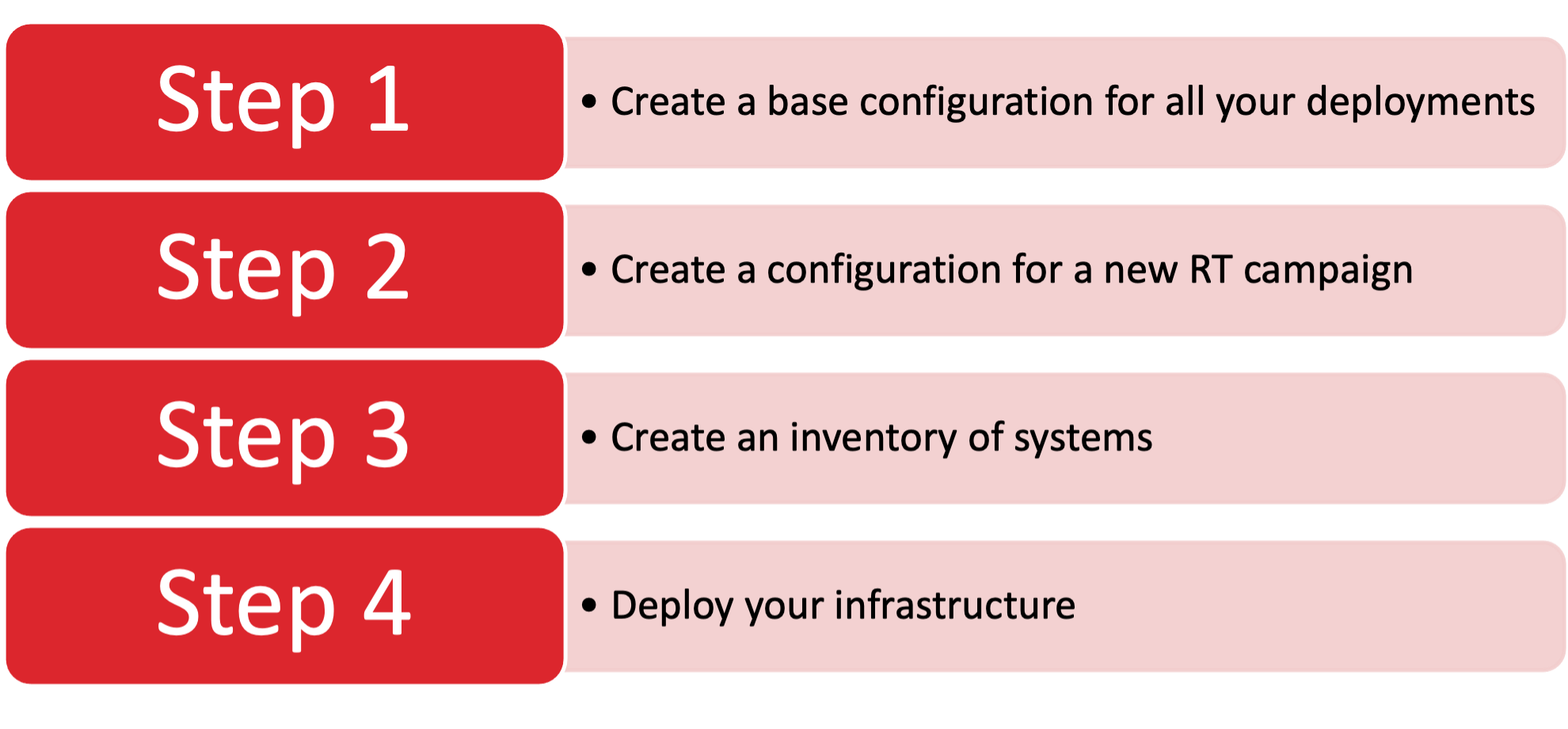
HOW TO GET STARTED?
For detailed instructions please follow the Readme in the GitHub repository. But on the high level it boils down to the following:
DESIGN PRINCIPLES
We built this tool with resilience in mind, ensuring an OPSEC-safe setup by retrieving all critical key material from the deployed servers, enabling you to rebuild and keep receiving your shells even if one of your servers crashes and burns. Red Wizard is mainly based on Ansible and Docker, making it easy to deploy and manage.
Other design principles can be summarized as follows:
- Simplicity trumps fanciness
- Operational Security (OPSEC)
- Must be robust
- No magical Black Boxes
- Everything must be self-documenting
- Easily extendable
- Preconfigured listeners / phishing profiles
- Log everything
The actual deployment follows the tried and tested approach for Red Teaming infrastructures where you have a backend / relay infrastructure:
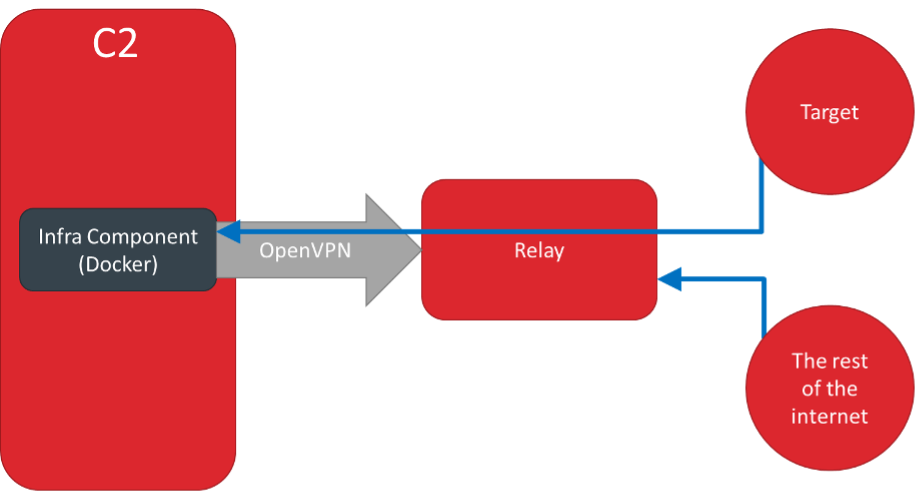
In this case there is a Command and Control server with for example a gophish instance. This gophish instance is exposed to the internet via a public relay. This relay decides, based on the URL and other featured whether this is an actual callback or other scans from the internet. A real callback will be forwarded to the backend, other internet traffic will not, improving the OPSEC of the Red Team.
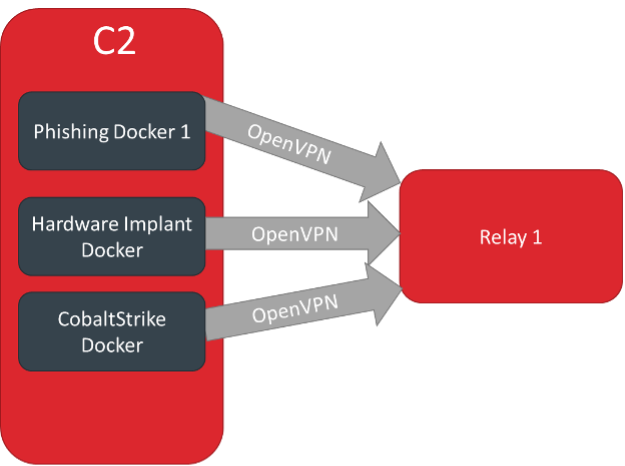
Red Wizard supports many deployment modes, for example multiple components that each call out to their own relay:
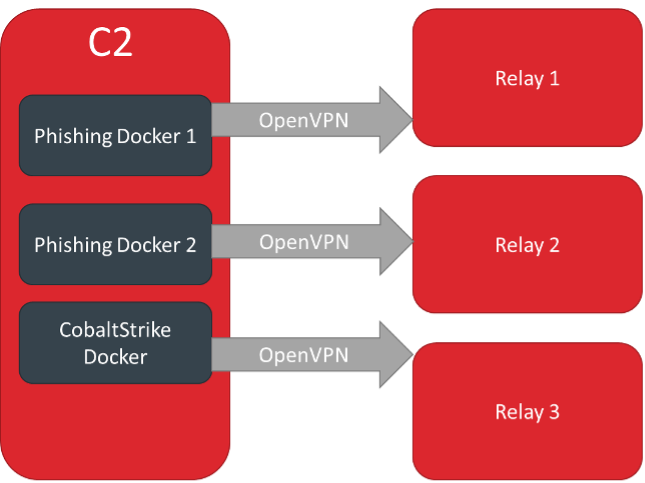
Or multiple components that share the same relay:
UP NEXT:
The next blog post will show you all the important features of a deployed Red Wizard infrastructure and help you create your first deployment.
ABOUT THE AUTHOR
Ben Brücker
Ben Brücker is Senior Security Specialist and Domain Manager Red Teaming at Secura. He studied Computer Science, Cyber Security and Artificial Intelligence at Radboud University in Nijmegen. For 8 years, Ben has been working at Secura. He specializes in Red Teaming and has led many successful Red Teaming assessments.
MORE INFORMATION ON RED WIZARD AND RED TEAMING
Would you like to know more about Red Wizard and our Red Teaming services? Please fill out the form and an expert will contact you within one business day.

ABOUT SECURA
Secura is a leading cybersecurity expert. Our customers range from government and healthcare to finance and industry worldwide. Secura offers technical services, such as vulnerability assessments, penetration testing and red teaming. We also provide certification for IoT and industrial environments, as well as audits, forensic services and awareness training. Our goal is to raise your cyber resilience.
Secura is a Bureau Veritas company. Bureau Veritas (BV) is a publicly listed company specialized in testing, inspection and certification. BV was founded in 1828, has over 80.000 employees and is active in 140 countries. Secura is the cornerstone of the cybersecurity strategy of Bureau Veritas.
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.





