Effective Penetration Testing: Aligning with Threat Intelligence to Raise Cyber Resilience
Modern Penetration Testing Challenges - by Paul Pols, Lead Ransomware Resilience at Secura/Bureau Veritas Group.
... > Vulnerability Assessment / Penetration Testing (VAPT) > Effective Penetration Testing: Aligning with Threat Intelligence to Raise Cyber Resilience
Author: Paul Pols, Lead Ransomware Resilience at Secura/Bureau Veritas
Modern Penetration Testing Challenges
A penetration test is only as effective as its ability to accurately emulate the complex and evolving cyber threats targeting organizations. Traditionally, penetration testing often remains narrowly focused on systems that organizations identify as the most valuable: their “crown jewels”. This limited focus may not fully align with the tactics and techniques of actual threat actors, who frequently exploit vulnerabilities in supporting systems to navigate through an IT infrastructure.
Modern cyberattacks often start with seemingly minor breaches that can significantly escalate. For instance, attackers could compromise an employee’s or supplier’s endpoint device or steal credentials for external interfaces. They could use these initial footholds to further penetrate the network through tactics such as privilege escalation and lateral movement. This enables them to access the crown jewels directly, with administrative privileges acquired elsewhere. Moreover, threat actors may target other systems within the organization that, while not considered “crown jewels”, are nonetheless crucial to the organization's operations.
This discrepancy underscores the need for a shift in how penetration tests are scoped and conducted, ensuring they cover broader and more realistic threat scenarios based on the latest threat intelligence about the tactics of relevant threat actors.
The Crucial Role of Threat Modeling
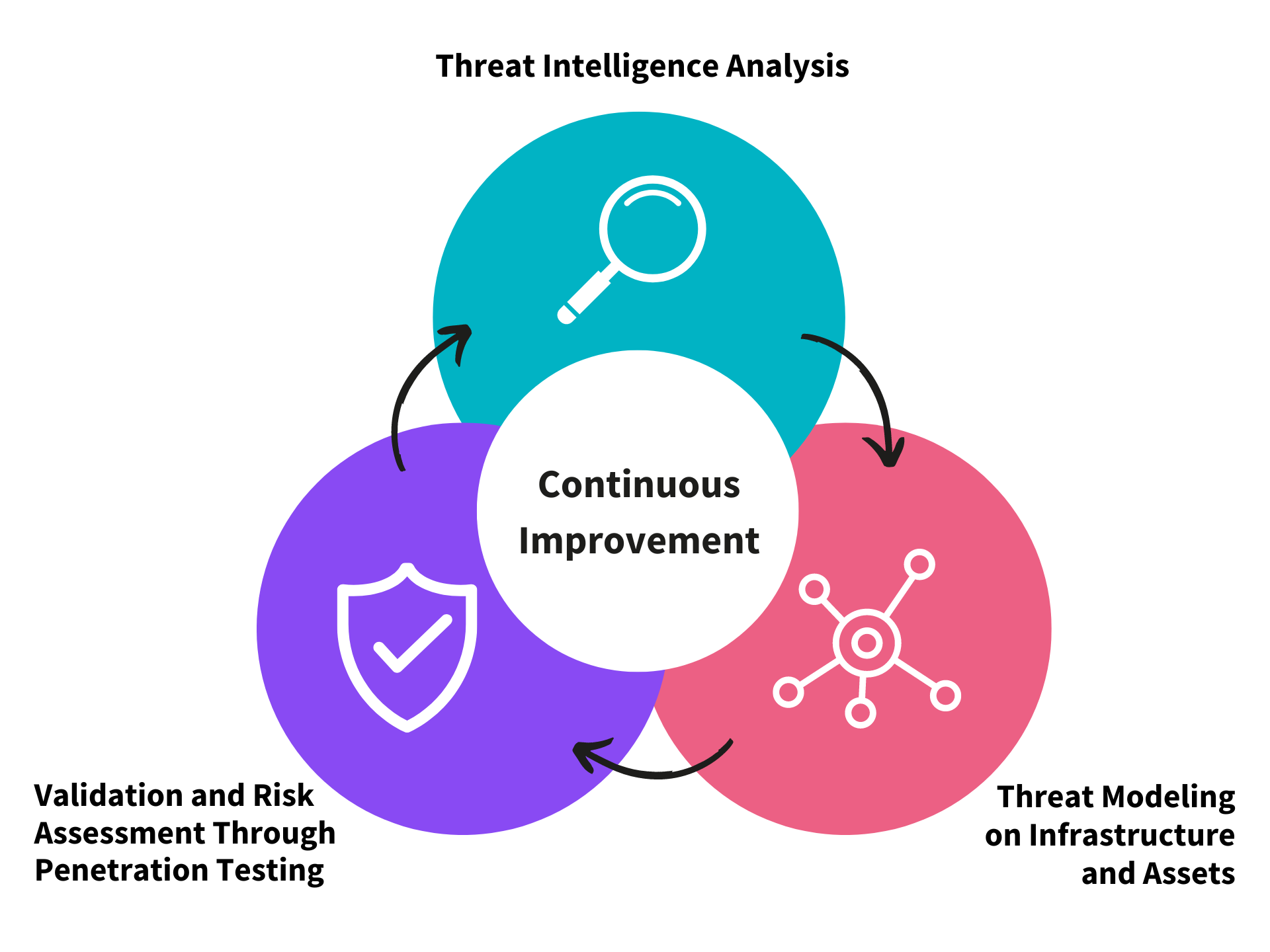
Threat modeling is a structured process that identifies potential threats within an organization's network, to understand the infrastructure from an attacker’s perspective and to develop robust defenses. Here’s a streamlined overview of the process:
Strengthen your cyber defenses with threat modeling and targeted penetration testing.
- Continuous Threat Intelligence Analysis: It is important to continuously monitor and analyze threat actors and their tactics, techniques, and procedures (TTPs). This intelligence helps identify which threats are the most relevant to specific organizations, typically influenced by the sectors in which they operate. We use this approach to tailor our threat models to better reflect the unique risks and challenges faced by each organization.
- Threat Modeling on Infastructure and Assets: Understanding the infrastructure and identifying critical assets that attract potential attackers help pinpoint relevant threats and likely attack paths. This analysis is crucial for mapping out where an organization is most susceptible to attacks based on the operational context and relevant TTPs. We typically perform this step through a threat modeling workshop with key stakeholders. The end result of threat modeling can often be a strategic roadmap or detailed penetration testing calendar, aligning future security testing with identified threats.
- Validation and Risk Assessment Through Penetration Testing: By simulating real-world attacks through penetration testing, we validate and complement identified threats and assess their potential impact and likelihood to determine their risk. This step is integral for prioritizing which threats need immediate attention and determining the effectiveness of current defenses. The results of penetration testing can guide strategies for risk mitigation, ensuring that security efforts are concentrated where they are most needed.
Frameworks such as STRIDE, the Unified Kill Chain, and MITRE ATT&CK™ provide structured methodologies for identifying and simulating the tactics an attacker might employ. Applying these frameworks ensures comprehensive assessments beyond obvious vulnerabilities, covering all aspects of organizational security.
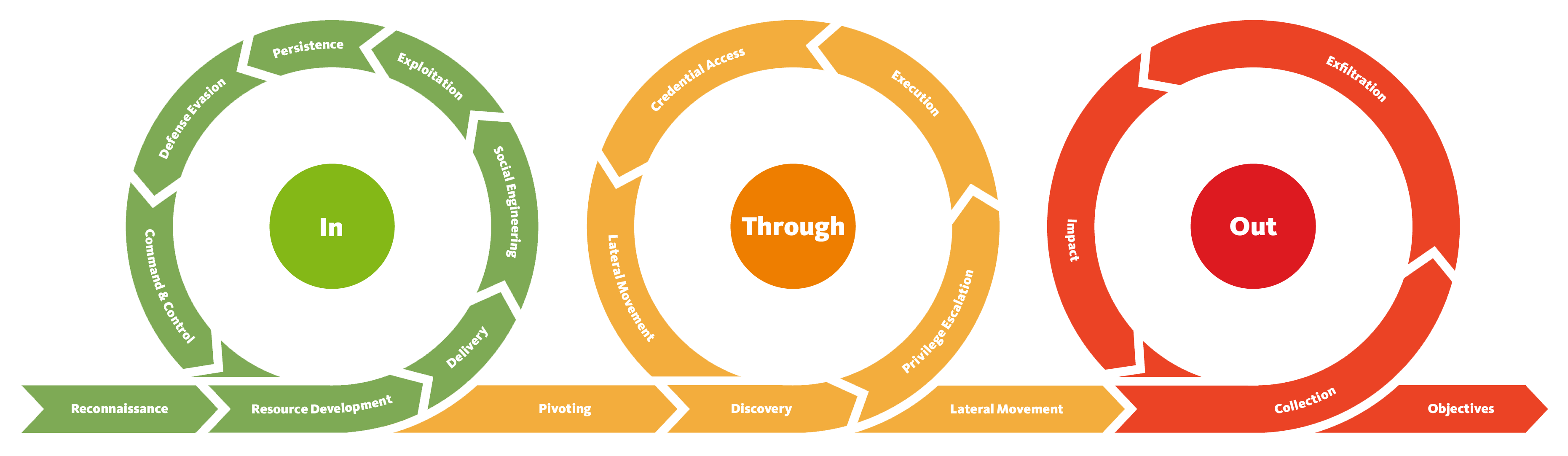
Unified Kill Chain (Source: Paul Pols)
Beyond Regulation: Implications for All Sectors
Certain regulatory frameworks mandate the incorporation of comprehensive threat intelligence into security testing, particularly within the financial sector:
- TIBER-EU, developed by the European Central Bank, promotes ethical red teaming guided by threat intelligence, aiming to enhance the cyber resilience of financial institutions.
- ART, developed by De Nederlandsche Bank, offers a more adaptable modular approach, allowing organizations to customize their testing components to meet their specific security needs and objectives.
- DORA's Threat Led Penetration Testing (TLPT) mandates that financial entities within the EU undergo extensive testing that simulates real-world attack scenarios to ensure that all aspects of an organization are resilient to cyber threats. As such, DORA’s TLTP will replace TIBER-EU with TLTP.
These frameworks exemplify how regulatory requirements shape more thorough and effective cybersecurity practices. Adopting frameworks and practices that incorporate threat modeling and comprehensive testing can provide significant benefits across all sectors, not just those regulated. It can also serve as a stepping stone for organizations new to this level of scrutiny, who are advised to gradually plan and scale their offensive security testing activities, as a full-scale TIBER-EU, ART or TLTP can be overwhelming.
Conclusion: Aligning Penetration Testing with Threat Intelligence
As cyber threats grow in complexity and sophistication, the need for adaptive and informed defense strategies becomes crucial. By weaving threat intelligence into penetration testing, organizations can move beyond the traditional focus on protecting their crown jewels in isolation. Instead, they can identify and address the specific risks most relevant to their unique environments to protect their crown jewels. This intelligence-driven approach makes penetration testing more effective and allows organizations to raise their cyber resilience against the ever-evolving cyber threat landscape.
This article was originally published in our Cyber Vision Series on LinkedIn about the changing nature of cybersecurity, and the future of cyber resilience.
About the Author
Paul Pols
Paul Pols, is Secura’s Ransomware Resilience Principal. Paul is also a lecturer at the University of Leiden for the executive master’s degree in Cybersecurity. He teaches network security with a focus on attack life-cycle and Kill Chain models, such as MITRE ATT&CK and the Unified Kill Chain. He developed the Unified Kill Chain threat model to describe attack paths, which can be used to analyze, compare, and defend against cyberattacks by advanced threat actors. Before he joined Secura, Paul also worked as a principal security expert and technical and legal advisor for the Investigatory Powers Commission (in Dutch: TIB) that reviews the exercise of special powers by the Dutch intelligence and security services.

More Information
Would you like to learn more about the modern pentesting approach? Please fill out the form below and we will contact you within one business day.
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.






