Advanced Red Teaming (ART)
For companies and organizations in the financial, healthcare and public sector, we offer our brand new Advanced Red Teaming (ART) service; a realistic attack simulation based on actual threat intelligence.
... > Red Teaming > Advanced Red Teaming
Protect your organization with Advanced Red Teaming (ART)
Advanced Red Teaming is a framework for threat intelligence based red teaming, developed by De Nederlandsche Bank. Advanced Red Teaming gives you strategic insight into your resilience against real world treat actors. It tests your defensive capabilities in depth. Do you want to conduct an Advanced Red Teaming project? Our experienced Red Teaming experts can help you.

Simulate a real cyber attack

Follow regulatory framework

Work with an experienced partner

YOUR CHALLENGES
- How do you keep up with evolving threats and new techniques that threat actors use to exploit vulnerabilities?
- How do you make sure all parts of your network, from cloud environments to interconnected systems, are resilient against attacks?
- How do you know if your detection works properly: do you know if you are being hacked?
- Do you know how your organization will respond when a detection occurs?
- How do you reach compliance with new cybersecurity regulations such as DORA?
Discover more about Advanced Red Teaming:
1. Four key elements of Advanced Red Teaming
2. The benefits of Advanced Red Teaming
3. How does ART relate to TIBER and TLPT?
4. How Advanced Red Teaming works
5. Different roles in ART
6. Our Red Teaming experts
Four key elements of ART
Advanced Red Teaming is intended for institutions in the financial, healthcare, telecom, energy and government sectors, allowing you to test how resilient your organization is against cyber attacks. An Advanced Red Teaming project is always based on current threat intelligence and is always conducted under the guidance and supervision of the relevant Managing Authority, such as De Nederlandsche Bank for the financial sector or Z-CERT for healthcare. Within healthcare ART is known as ZORRO.
Four key elements of any Advanced Red Teaming project are:
- Secrecy. As few people as possible within your organization are aware of the project.
- Live systems. The Red Teaming is performed on live systems, so that the attack simulation is as realistic as possible.
- At least 1 scenario involves ethical hacking.
- The scenario must be based on threat intelligence.

Ben Brücker
Domain Manager Red Teaming
Secura
ART is a very sensible and practical modular framework for high quality Red Team assessments. Performing these assessments will result in critical insights on how resilient your organization is to real world threat actors.
Benefits of Advanced Red Teaming
Improve your detection and response capabilities: By simulating real-world attacks, you can train your security team under controlled conditions, improving their readiness and response times to actual cyber threats.
Focus on areas of highest risk: The modular nature of the ART framework means it can be customized to fit the needs of your organization. As a result, you can focus resources on the areas of highest risk and greatest value, making the project more efficient and aligned with business priorities.
Start your compliance journey: Using a framework like ART can help you demonstrate compliance with industry standards and regulations.
How does ART relate to TIBER?
Advanced Red Teaming builds upon the foundation established by the Threat-Intelligence Based Ethical Red-teaming (TIBER) framework, which has been in use since 2016. TIBER has been focused on testing the cybersecurity of core financial infrastructures like banks and payment institutions. There are a few significant differences between ART and TIBER:
- ART is more flexible and modular compared to TIBER. It has both mandatory and optional parts. This means that organization can fit ART in their budget, learning goals and security posture.
- TIBER is specifically designed for the financial sector, while ART is suitable for a broader range of organizations.
- ART is a voluntary framework, while TIBER is mandatory for core financial institutions in The Netherlands. TIBER is set to become part of the European law DORA under the name Threat-Led Penetration Testing (TLPT), starting in January 2025.
How Advanced Red Teaming works
An Advanced Red Teaming project has three phases, as pictured below: preparation, testing and closure. Each phase has a few mandatory modules that can be supplemented with optional modules.
During an Advanced Red Teaming Project the relevant Managing Authority plays a central role. They play the part of impartial referee, ensuring the processes and giving input on feasibility.
This graphic relates specifically to ART for financials. The ART process for healthcare (ZORRO) is similar, but differs on details.
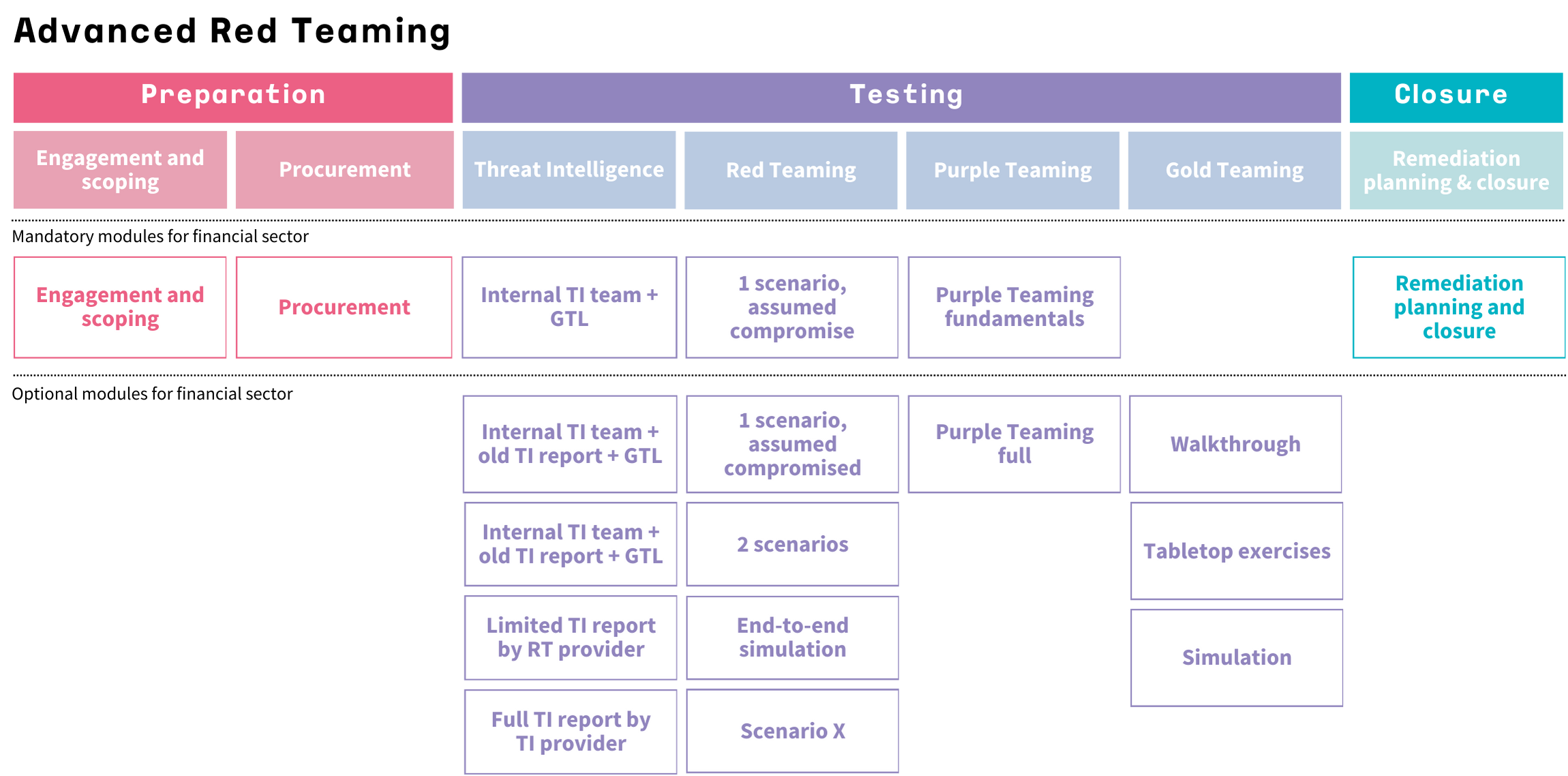
The Process of Red Teaming
01
Phase 1 - Preparation
The preparation phase of Advanced Red Teaming involves both the Managing Authority of your organization (i.e. DNB or Z-CERT) and your security provider, but both are involved at different times. You will first determine the scope and the different modules of your Advanced Red Teaming project with the Managing Authority. You then discuss this plan with our experts.
02
Phase 2 - Test Phase
Threat intelligence - Because each ART project is based on current threat intelligence (TI), the test phase starts with collecting relevant TI. How this TI is collected depends on your sector and needs. For instance: in the healthcare sector the TI is provided by Z-CERT. The TI report can be either basic or full-fledged, based on the modules you choose.
Threat led attack - We then move to the actual Red Teaming, which will cover at least one scenario. Our Red Team will devise scenarios with you that fit the threat intelligence profile and will try to reach your crown jewels without detection by your defenders or Blue Team. This attack is structured around the MITRE ATT&CK framework.
Purple Teaming - After the attack it is crucial to discuss the attack with your defenders to find out what went well and which room there is for improvement. This collaboration between Red and Blue Teams is called Purple Teaming. Each ART project has at least a fundamental Purple Teaming element. Towards the end of the assessment, the Managing Authority will assess whether the fundamentals are adequate, or if the Purple Teaming should be extended.
Optional: Gold Teaming - You can use the outcome of the Red Teaming exercise to train your crisis teams. This is called Gold Teaming. For instance, you can use the outcome to create a Walkthrough, a Tabletop or a complete Simulation for your crisis teams.
03
Phase 3 - Closure Phase
Once the attack is over, the so-called closure phase begins. This stage does not only mean managing the leftover digital remnants of the executed attacks. It also means remediation planning. What are the best steps for follow-up? We give you complete and thorough feedback of our findings and also give you concrete recommendations.
Different roles in ART
Red Team
The Red Team is the attacking team. It consists of multiple experienced Red Teaming experts from Secura.
Blue Team
The Blue Team is your organization's defending team. It is responsible for defending the networks, systems, and applications. This team is unaware of the Red Teaming simulation, to increase realism and test response.
Control Team
The Control Team acts as the link between the Red and Blue Teams and is informed about all attacks from the Red Team. It consists of employees from both your organization and from ours. The representative of the Managing Authority (for instance DNB or Z-CERT) is also present at all Control Team Meetings. However, this person is technically and legally not part of the Control Team.
Purple Team
A mandatory part of Advanced Red Teaming is so-called Purple Teaming: the Red and Blue Teams meet after the simulation to discuss and learn from the attack.
Our Red Teaming experts
An attacker uses a vast arsenal of tools to abuse all aspects of your digital security, technology, physical security, and human behavior to access your most important crown jewels. To mimic this type of attack requires a team of experienced hackers and social engineers with the proper knowledge, broad experience, and many specialties. We have built this knowledge, experience, and specialties into its team over the past twenty years.
Over the past years we have conducted around 35 Red Teaming projects each year. Many of these were complex simulations, for instance on critical infrastructure. Our team is experienced in the three security domains: technology, physical security and human behavior.
Our Red Teamers hold relevant certifications such as Certified Red Team Professional (CRTP), Certified Red Team Operator (CRTO), Certified Red Team Expert (CRTE), Master Level Social Engineer (MLSE), and many others.
Plan your ART now
The regulations that require some form of red teaming, such as DORA, are in the final stages of implementation. The number of security companies that can conduct these projects is limited. In practical terms these means it is wise to start planning your ART project now, before our experts are fully booked.
DOWNLOAD brochures

Secura Red Teaming Fact Sheet
What is Red Teaming? What are the different teams and types of red teaming?
DownloadContact me about red teaming
Would you like to learn more about our Red Teaming Assessment? Please fill out the form below, and we will contact you within one business day.

Related Services
Tabletop Cyber Crisis Management
Social Engineering Services
Hacker Mindset Workshop
Secura CyberCare
Ransomware Resilience Assessment
Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.