OT Cybersecurity Fundamentals Training
... > Training Courses > OT Cybersecurity Fundamentals Training
OT Cybersecurity Fundamentals Training
24-25 SEPTEMBER 2025 | AMSTERDAM
Industrial Control Systems (ICS) form the backbone of everyday life, underpinning everything from critical infrastructure to building automation. This course has been designed to provide you with insight into the ICS security landscape in order to equip you to assess and defend industrial control systems.
TWO DAY COURSE
Date: 24-25 September 2025
Location: Secura Office, Amsterdam
Price: €1.200 excl. VAT
* Note: We also offer this training as an in-company option. Contact us for more information.
OT Fundamentals Training
If you are interested in this training, please fill out the form and we will contact you within one business day.
Why should you attend?
- Gain a basic understanding of ICS fundamentals: industrial processes, architectures, equipment, and protocols.
- Get familiar with OT cybersecurity challenges and why they differ from regular IT environments.
- Learn about ICS threats, relevant attack surfaces, common vulnerabilities, and the required attacker capabilities to exploit them.
- Become familiar with the root causes behind several high-profile real-world ICS incidents and learn from the security failures enabling them.
- Learn how to apply threat modeling in ICS environments.
- Learn how to navigate applicable standards and apply effective security controls.
Xander Prins
Gemeente Rotterdam
The technical parts were difficult, but gave a good insight of the possibilities. Loved the models. It gives me a good background to participate in the OT Resilience project
Intended Audience
This course has been designed as a general introduction to OT cybersecurity, and it is, therefore, suitable for a broad audience. It will benefit everyone: from management requiring a high-level overview of the complexities of this challenging domain to seasoned control system engineers and IT & OT security personnel.
Required Skills & Expertise
Basic understanding of common computing & networking technologies and fundamental security principles and concepts (CIA triad, access control, firewalls, etc.) is recommended.
Program
The program is divided into four modules, which are given in a two-day course. Each module consists of a theoretical part, real-world examples, and practical illustrations. After completing the course, each participant is rewarded with a certificate.
Day 1
Module 1: Introduction to ICS
- The program starts with a walkthrough of ICS fundamentals: Basic terminology, Industrial processes, control theory, and plant organization basics.
- The differences between IT and OT are highlighted, focusing on potential cyber impact in the OT environment.
- Participants will be shown how a simple control loop operates in a lab setting and learn the history of ICS security
Module 2: ICS Components and architecture
- In this module, we will dive into the Purdue model and all the components that can be found in typical ICS networks. From instruments to PLCs and from safety controllers to historians, all devices are discussed in detail, including their common cyber weaknesses.
- Next, we will explore how all these components form a system by discussing network components, industrial protocols, network architectures, and of course, their weaknesses.
- This discussion will be richly illustrated by examples and lab demonstrations of vulnerabilities affecting widely deployed ICS equipment using our “OT Box”.
- This is a demo environment consisting of current ICS equipment which accurately represents the workings of an actual ICS control loop.
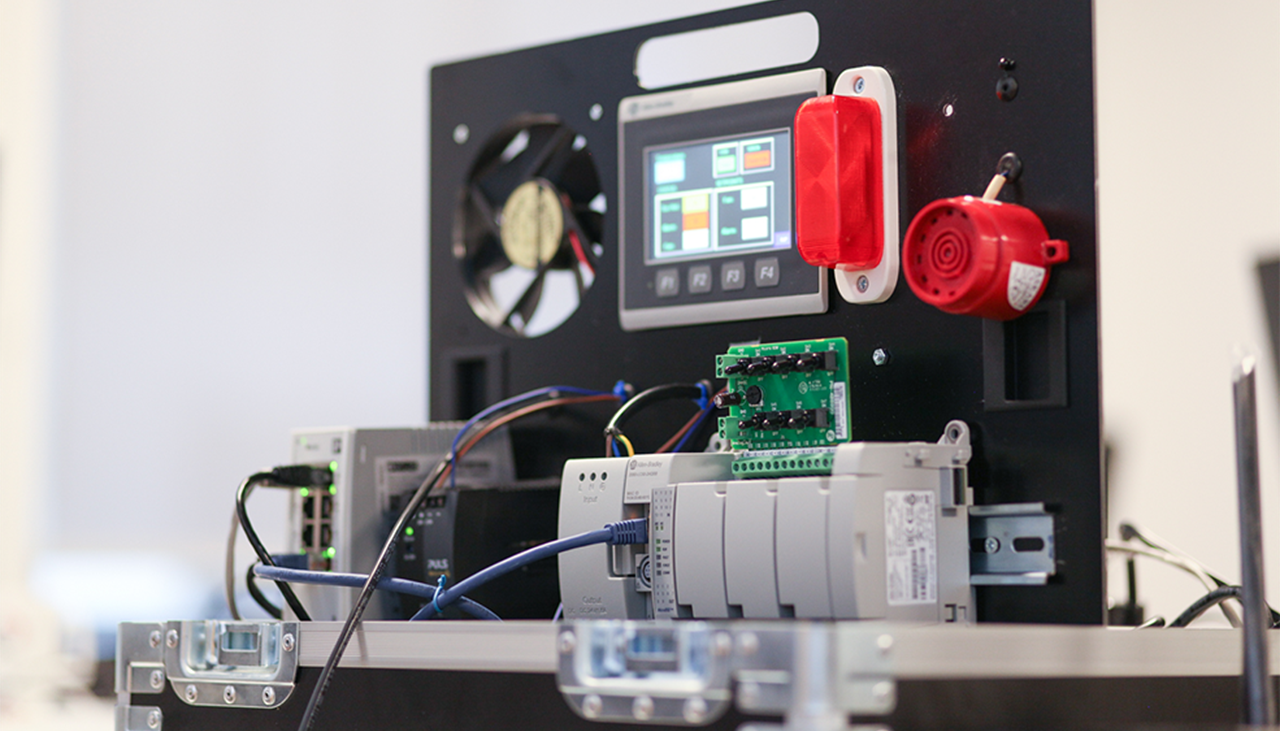
In the training we will use our OT Hackbox to demonstrate vulnerabilities affecting widely deployed ICS equipment.
Day 2
Module 3: ICS threat landscape, Cyber-Physical Attacks & Attack Surface
After a brief recap of the first day, we will delve into the ICS threat landscape and take a look at attacker motives and capability and impact factors in assessing the cyber risk properly.
Whether the concern is targeted industrial espionage or destructive cyber-physical attacks, we will walk attendees through the complexities of attacker activities.
This entails process comprehension and damage scenario design in order to properly analyze the potential cyber-physical impact and the required attacker capabilities.
Finally, we will explore the vast attack surface of industrial control systems:
- Breaching perimeters to lateral movement and pivoting across network segments in order to impact the process through the exploitation of industrial protocol insecurities
- Compromising workstations, databases, controllers, and field devices.
During interactive discussions, we will discuss how bad these typical OT security issues are in practice and how we could mitigate these issues.
Module 4: Security Standards, Threat Modelling & Real-World Case Studies
- First, attendees will learn how to navigate standards like IEC 62443 and how to integrate the perspectives and knowledge gained during this course into applying effective security controls and risk management strategies.
Next, we introduce threat modeling as a technique to learn to look at an ICS environment through the eyes of an attacker. Because when you want to defend against attackers, you’ll have to think like them. - The same OT Box we hacked in module 2 is used during an interactive threat modeling session to collectively find all possible attack vectors.
Finally, the content of the entire course will be correlated with real-world case studies, such as the Stuxnet and TRITON attacks, and we will discuss the lessons learned from these well-known incidents.
One of the best training courses I ever attended regarding cybersecurity - good balanced coverage of the different topics that need to be addressed.
Meet The Trainer
Dominika Rusek Jonkers
Dominika Rusek Jonkers is Senior Security Specialist at Secura. She brings over 10 years of expertise in industrial cybersecurity.
Her extensive experience spans technical assessments of Industrial Control Systems (ICS), penetration testing, Tactical Network Exploitation (TNE), Red Teaming (including Active Directory compromise), and executing remediation programs. These include implementing ICS monitoring solutions, such as Claroty, Nozomi, and CyberVision, as well as designing robust network segmentation strategies.
Dominika’s skill set also includes hardware hacking on IoT/IIoT devices and advanced threat hunting in ICS networks.
Her passion for knowledge sharing is evident in her role as a trainer, where she facilitates dynamic courses on topics like OT security fundamentals, ICS technical assessment methodologies, and ICS monitoring crash courses.
More Information & Registration
If you are interested in this training, please fill out the form and we will contact you within one business day.

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.






