Tailored phishing
Recently, Jellema and her colleagues have been seeing more ‘tailored phishing’: large-scale, automated phishing, using tailor-made emails or text messages. ‘Criminals scrape information from social media for this purpose. The message seems totally meant for you. It’s not just: ‘Hey, first name, last name,’ but also: ‘You’ve been working for this company for 4 years now.’ Romy Schellekens, a member of our team, is currently doing research on tailored phishing - together with the faculty of Mathematics and Computer Science of the TU Eindhoven. Our hypothesis is that a lot more people click on links in these types of e-mails.’
Baiting
Whatever form of social engineering is involved, according to Jellema it’s always about gaining trust or piquing your interest. With baiting, the social engineer uses ‘bait’, as the name suggests: ‘For example, I might attach an interesting attachment to an email and ‘accidentally’ send it to the entire company. Perhaps the file name is ‘Bonuses management next year’. My malware is hidden in that file.’
Pretexting
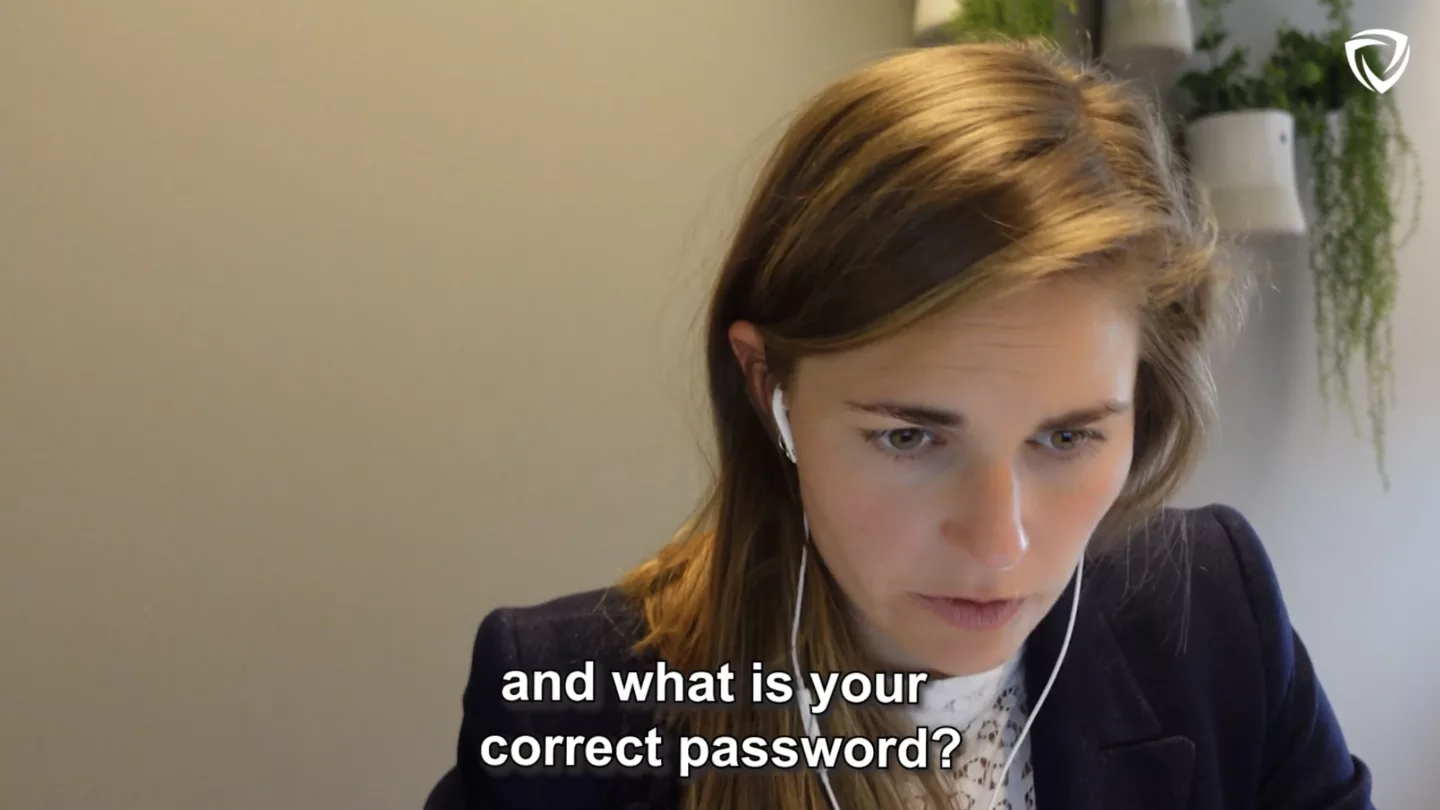
Pretexting means pretending to be someone else to gain trust. This often involves several steps. A social engineer might pose as your daughter. She is texting from a different number because her phone has been stolen. Once you believe that pretext, the social engineer will ask if you could to transfer money to ‘a friend’s account.’ Because not only the phone was stolen, but also the wallet.
5. Are there other examples of social engineering?
A social engineer often uses technology to hack people. But you can also get the job done without using a computer or telephone, says Jellema: ‘I sometimes work as a mystery guest. I literally get paid to break in. For instance, I did a job at a museum recently. The assignment was: how far can you penetrate the building? When someone opened a door with their access pass, I put my foot in the door. That’s how I got into the corridor that led to the restoration studio.’
Bathroom stall
An assignment like this can be quite nerve racking, says Jellema: ‘This corridor was hermetically sealed. I saw a camera. A bit further along was the guard booth. Nowhere to hide except a bathroom. So: I hid in a bathroom stall for 10 minutes. In the end, the chief guards intercepted me and didn’t let go of me. That’s what you want: don’t let me out of you sight. You can drop me off at reception, but if you leave me alone, I won’t stay put – just like an actual social engineer.’
6. What can you do against social engineering?
You’re at the office and you see someone who doesn’t belong there. What should you do? Jellema advises: ‘Don’t let people without a pass enter the building with you. That might feel a bit rude, but I always tell strangers who try to follow me in: ‘I’m sorry, but we agreed to keep this building safe together. So I can’t let you in if I don’t know what you’re doing here.’
To reception
If a stranger is already inside the building, and the situation feels safe: speak to them. Say, ‘Excuse me, I don’t know you. What are you doing here?’ If someone seems to be unauthorized, escort them to the reception or to a contact person, if they mention one. There’s no need to handcuff someone. Keep it friendly.’
Report it
You might be on the phone with someone, and you don’t trust them. In that case Jellema advises: ‘Don’t share information. If you already have: end the conversation and report it as soon as possible to someone who can investigate.
In The Netherlands we have the catchphrase, ‘Stop, hang up, call your bank.’ Please do! Did you click on a weird link on your work laptop? Call IT. Anyone can be distracted on a Friday afternoon. It happens to me as well: I fall for phishing emails. But report it.’