What Can Be Pentested?
... > Vulnerability Assessment / Penetration Testing (VAPT) > What Can Be Pentested?
What Can Be Pentested?
Over the decades, our customers have asked us to perform security tests on virtually every thinkable target. Some types of systems require extremely specific knowledge of the target, while others can be handled in much more generic ways.
That's why, while we definitely can perform, for instance, a penetration test on a bespoke application in a High-Performance Computing (HPC) environment, usually our customers ask to test their systems in environments that are more common. To give you an idea of the targets we test frequently, a selection is provided here.
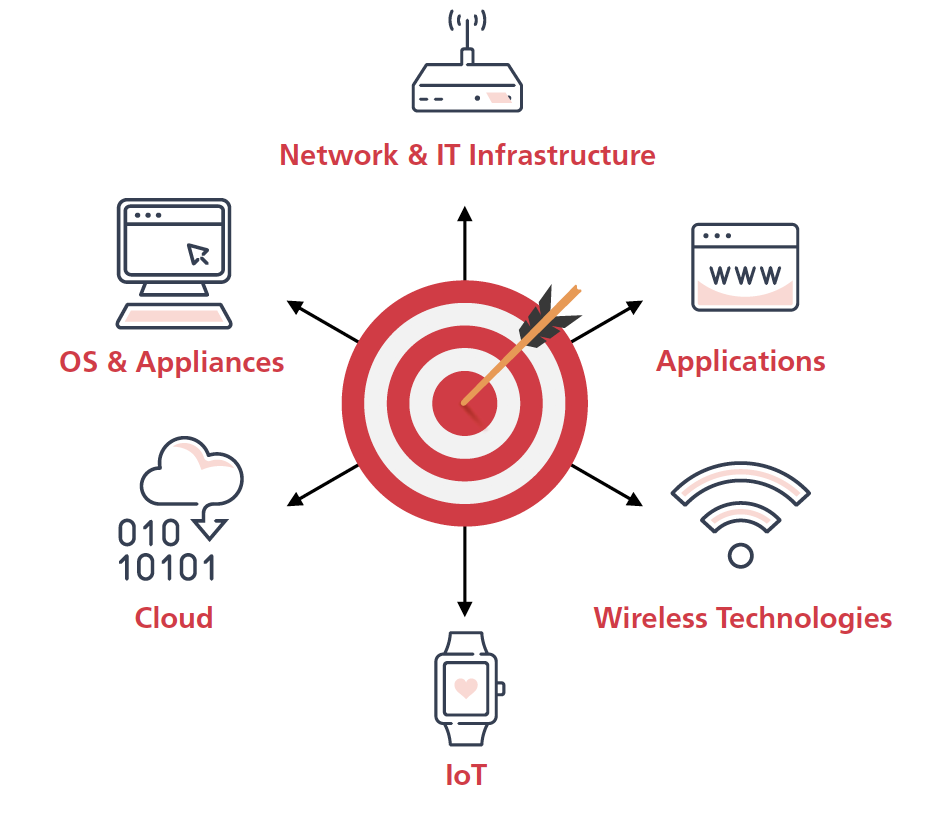
Which targets and technologies can you pentest?
Download Fact Sheet

DOWNLOAD FACTSHEET
Explains the scope, targets and technologies of Vulnerability Assessments and Penetration testing
DownloadPentest Services
Cloud Pentesting
Internal Network Pentesting
Mobile Apps Pentesting
Web Applications / API's Pentesting
Wi-Fi Pentesting
Hardware / IoT Pentesting
Infrastructure Pentesting
I'd like to know more about what can be pentested

Why choose Secura | Bureau Veritas
At Secura/Bureau Veritas, we are dedicated to being your trusted partner in cybersecurity. We go beyond quick fixes and isolated services. Our integrated approach makes sure that every aspect of your company or organization is cyber resilient, from your technology to your processes and your people.
Secura is the cybersecurity division of Bureau Veritas, specialized in testing, inspection and certification. Bureau Veritas was founded in 1828, has over 80.000 employees and is active in 140 countries.








